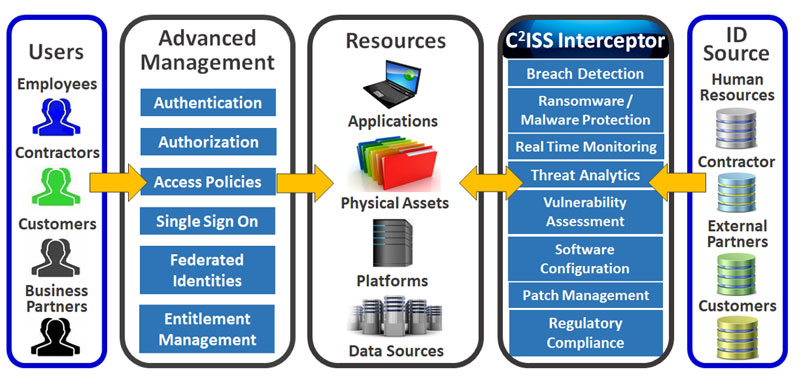
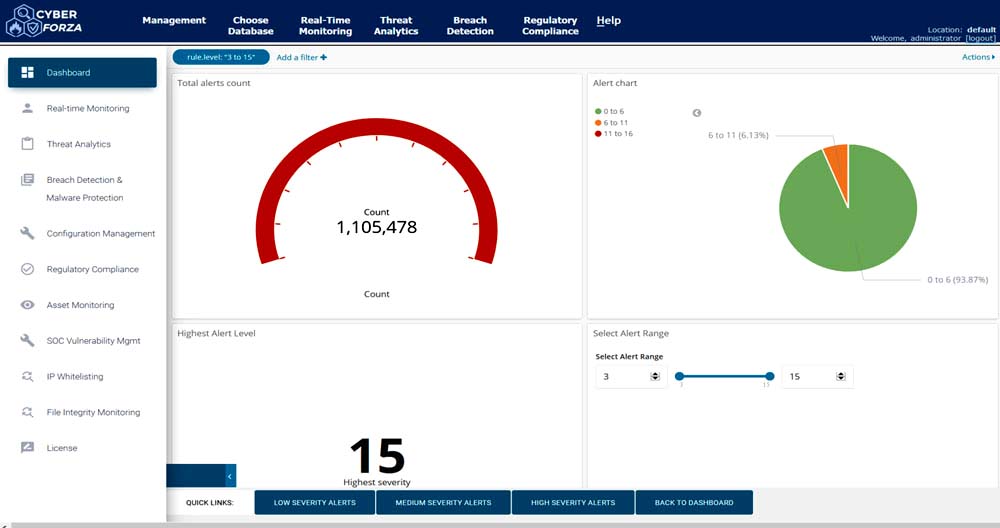
Interceptor Overview
Integrated Cloud AI Security Software defends Multi-Layer & Mult-Cyberattacks. Integrates 40 modules with single pane of glass for holistic visibility. Deployed in AWS, Azure, GCP, and Century Link Cloud. Supports On-Premise, Hybrid and Cloud.