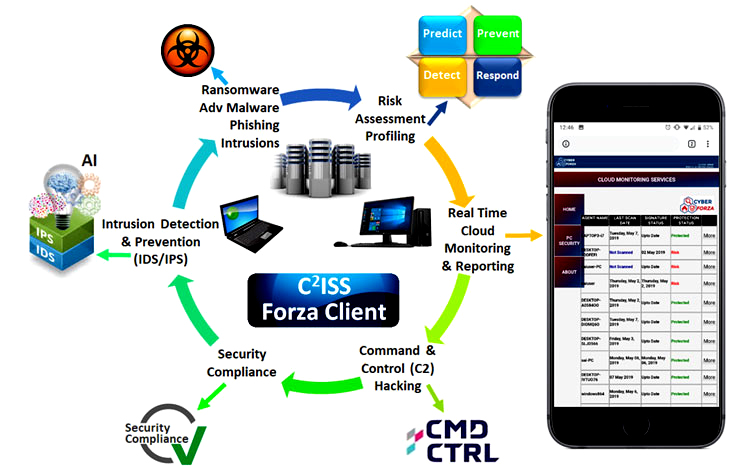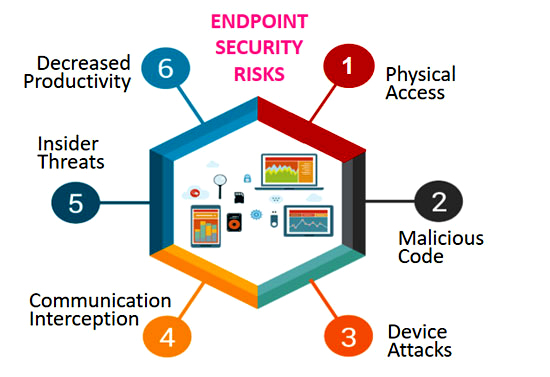
Ransomware attacks are trending upward as evidenced by the WannaCry and Petya outbreaks. Does your organization endpoint solution is protecting against Ransomware attacks?
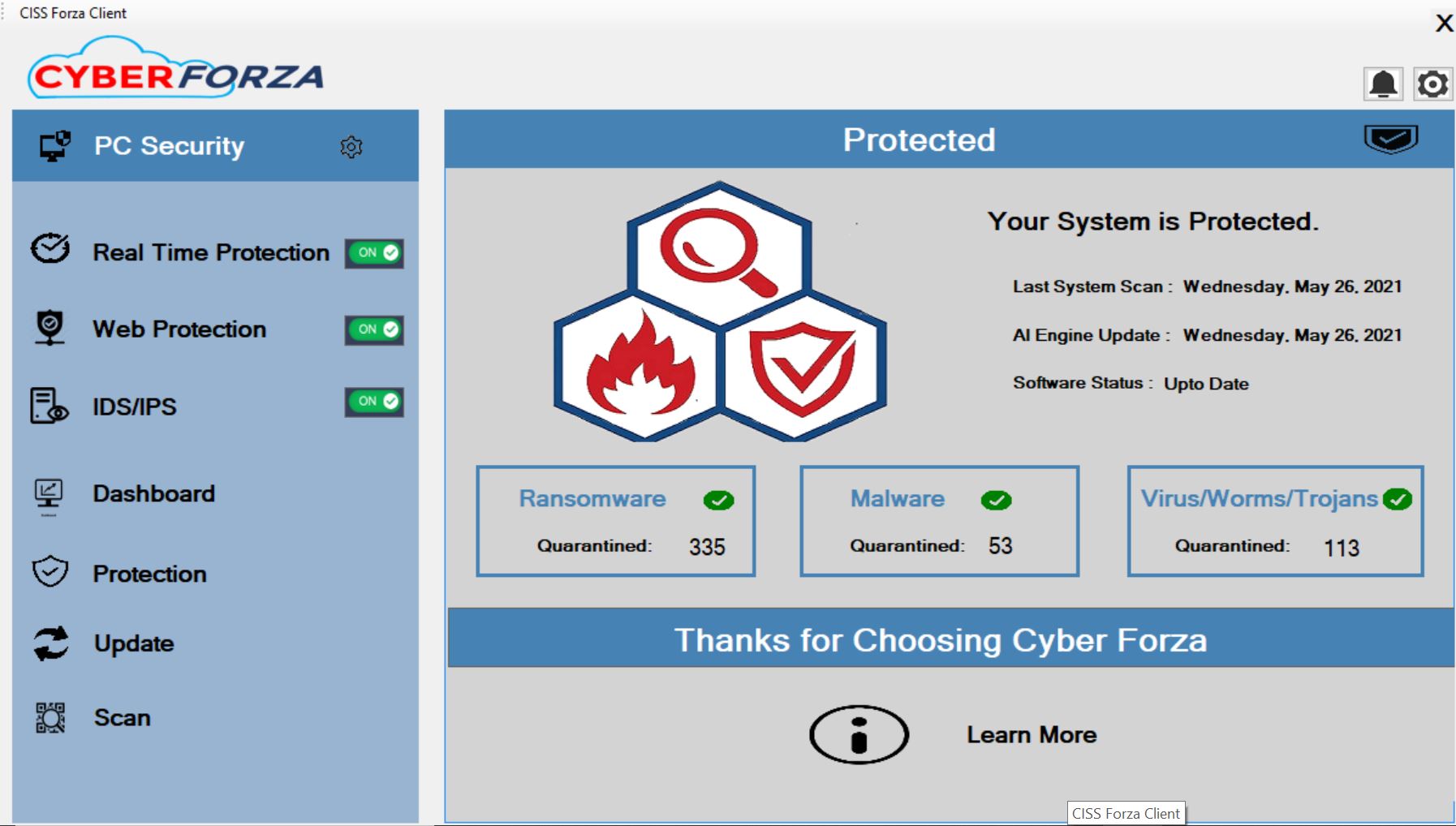
Forza Client defends Ransomware & Advanced malware attacks. Zero-day attacks & Honeypots fast detection capapbility.
Your present large foorprint endpoint solution consumes more system resoruces & impacts performance?
Forza Client provides the smallest footprint consumes less than 3% of the system resources.