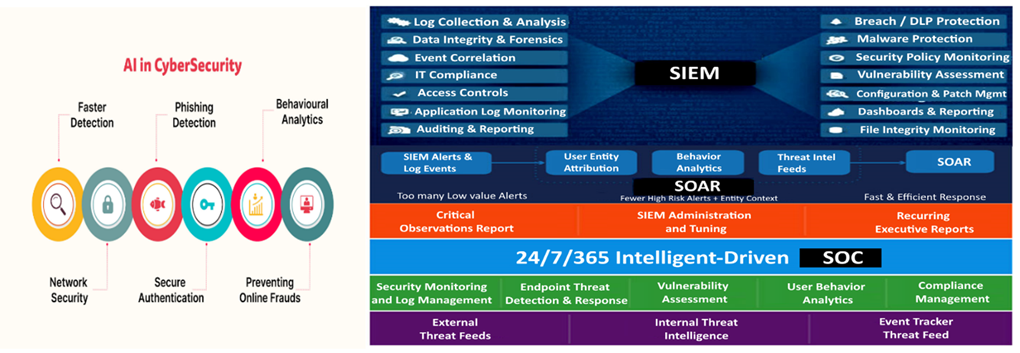
The Integrated AI Cloud Cybersecurity Operations Platform (“AI SEC OPS PLATFORM”) is a next-generation AI cloud-native security solution that consolidates critical defensive capabilities: including SIEM, SOC, SOAR, EDR, MDR, IDS, and AI Advanced Anomaly detection forms a unified AI-powered operations Platform. By eliminating security airgaps in the cloud, network environments, end points the platform enables proactive and intelligent threat prevention, detection, response, and remediation across small/medium enterprise infrastructures.

AI SEC OPS PLATFORM differentiates by offering a fully integrated cloud-to-endpoint security stack with end-to-end AI-assisted monitoring and response. It reduces the need for custom integrations and reduces operational overhead..
Our unified security platform delivers end-to-end protection across cloud, network, and endpoints with AI-driven threat detection and autonomous response. Reduce operational complexity and costs with a single integrated dashboard, while staying audit-ready with turnkey compliance support. Designed for hybrid and multi-cloud environments, our AI continuously adapts to evolving threats, giving you confidence and scalability without constant manual intervention.
Vulnerability and Risk Management Platform delivers continuous visibility, intelligent risk prioritization, and compliance-aligned decision-making across the entire Small/Medium business organizations. By correlating vulnerabilities at the OS, network, application, DevOps, AI Code, Open Source Code and product code levels, the platform enables organizations to focus remediation on what truly matters, reduce breach likelihood, and demonstrate compliance with recognized Risk Management Frameworks (RMF).
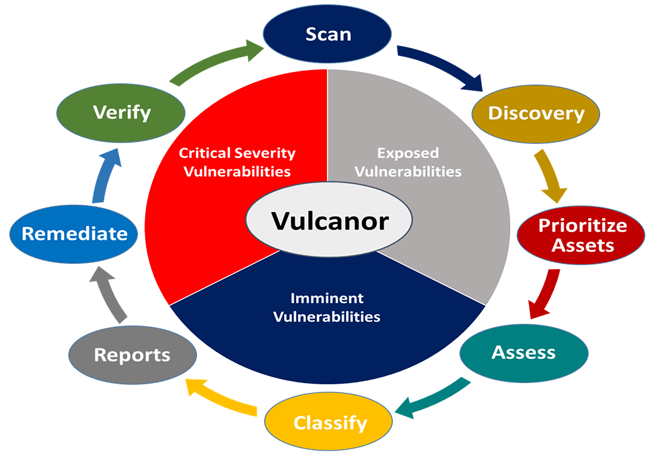
1. Unified Full-Stack Visibility
Tagline: "Security, Risk, and Compliance—Simplified. Prioritized. Actionable."
Problem: Traditional perimeter security, static IAM, and siloed monitoring tools cannot establish continuous trust across modern hybrid environments that include cloud, remote users, devices, OT, and IoT resulting in blind spots, lateral movement, and compliance gaps.
Zero Trust platform that continuously establishes trust and enforces dynamic access across users, devices, data, IT, OT, and IoT—based on real-time risk and behavior. A unified Zero Trust and Identity Access Management compliance platform that continuously establishes, verifies, and enforces trust across users, devices, data, applications, IT, OT, and IoT environments based on real-time risk, behavior, and context. This platform designed for small and medium size customers.
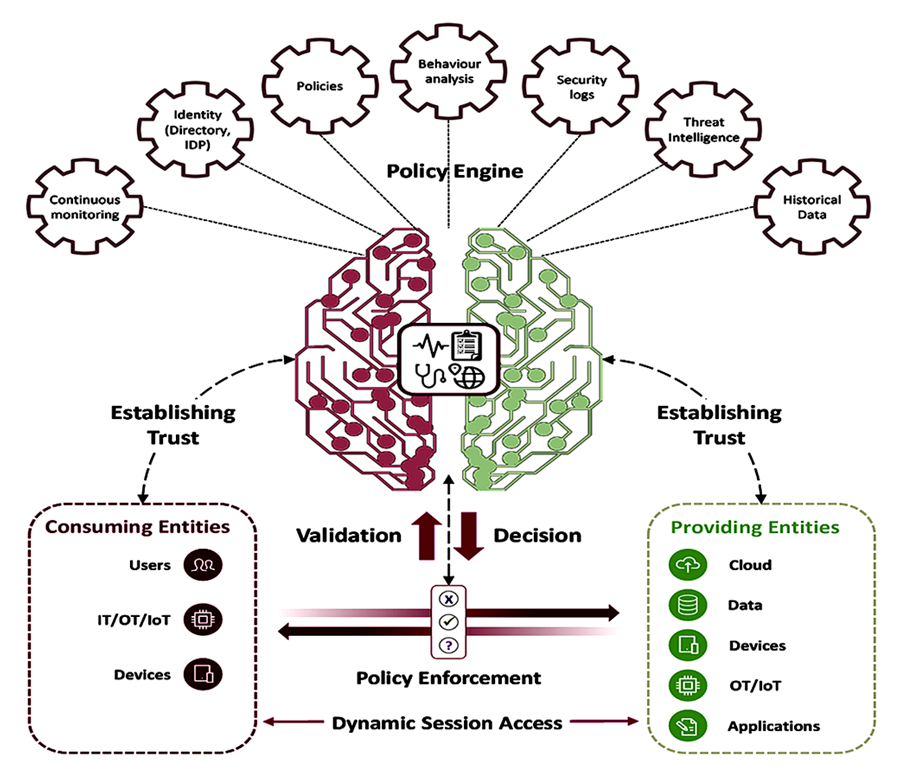
Our Zero Trust Platform continuously establishes confidence and trust for users, devices, data, and applications before, during, and after access is granted.
1. Continuous Trust Verification
Trust is never assumed. Users, devices, applications, and data are continuously verified in real time, with anomaly detection and dynamic access adjustment.
2. Unified Zero Trust Across IT, OT, and IoT
A single Zero Trust policy and enforcement model secures IT, OT, IoT, cloud, and data environments eliminating silos and complexity.
3. Dynamic, Risk-Based Authorization
Access decisions adapt instantly to risk. Cyber Forza closes traditional VPN security gaps by continuously validating identity and context beyond static authentication.
4. Password-less Advanced Authentication
Frictionless, high-assurance authentication using facial recognition and biometric identity no passwords required.
5. Real-Time Adaptive Policy Enforcement
Security policies automatically evolve based on user behavior and threat context, powered by an Agentic AI-driven enforcement model.
"Empower your organization with continuous trust and risk reduction, enforcing dynamic least-privilege access everywhere. Simplify security across hybrid environments with unified architecture, built-in compliance, and audit readiness while gaining real-time visibility to detect and remediate threats faster, cutting both risk and operational overhead."
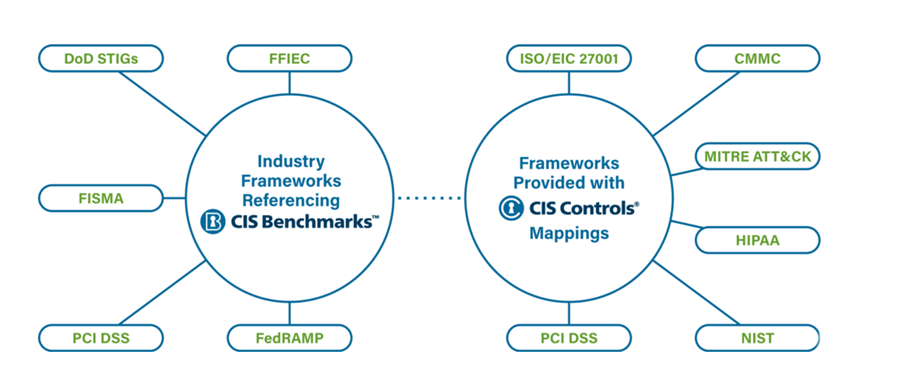
A comprehensive Cybersecurity Compliance and Audit Enablement platform delivering end-to-end compliance establishment, continuous monitoring, and audit readiness for organizations pursuing or supporting Federal, State, and Local Government contracts. The solution aligns security controls with mandated regulatory frameworks to reduce risk, accelerate certification, and sustain compliance through managed services.
Trust is never assumed. Users, devices, applications, and data are continuously verified in real time, with anomaly detection and dynamic access adjustment.
Copyright 2026 Cyber Forza.